A Blank Policy Template for IT Security provides a foundational framework for organizations to develop comprehensive security guidelines tailored to their specific needs. This template outlines essential sections such as access control, data protection, and incident response procedures to ensure robust cyber defense. Utilizing a blank template streamlines the creation of consistent and compliant IT security policies.
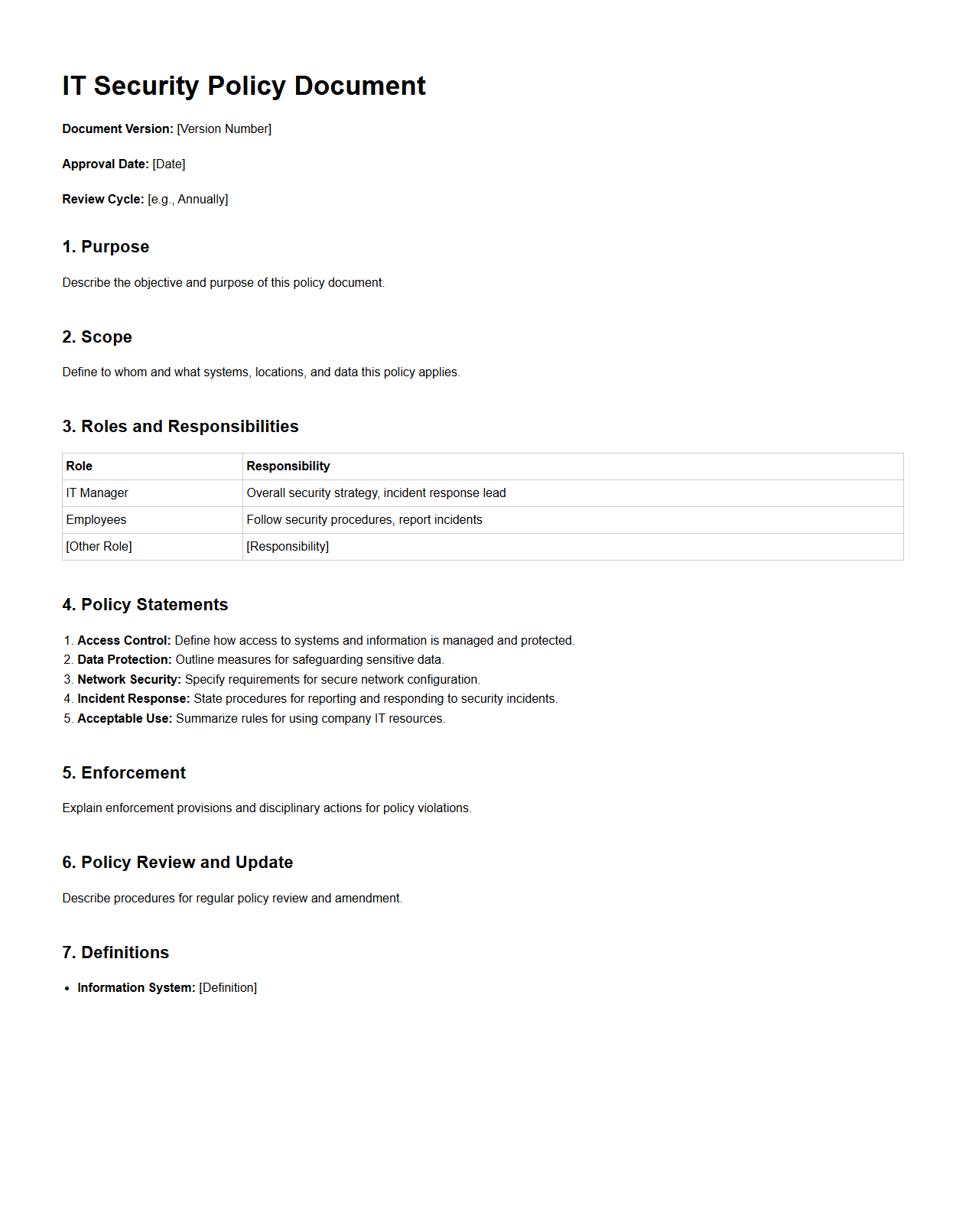
IT Security Policy Document Template
An
IT Security Policy Document Template serves as a structured framework that outlines an organization's essential security rules, procedures, and responsibilities to protect digital assets. It provides standardized sections covering topics such as access controls, data protection, incident response, and compliance requirements to ensure consistent implementation across all departments. Utilizing this template helps businesses maintain regulatory adherence, reduce risk of cyber threats, and promote a secure information technology environment.
Information Security Policy Framework Template
An
Information Security Policy Framework Template document serves as a structured guideline for organizations to develop, implement, and manage their information security policies effectively. It outlines essential components such as access control, data protection, incident response, and compliance requirements, ensuring consistent and comprehensive security practices. This template helps organizations align their security measures with industry standards like ISO/IEC 27001, enhancing risk management and regulatory adherence.
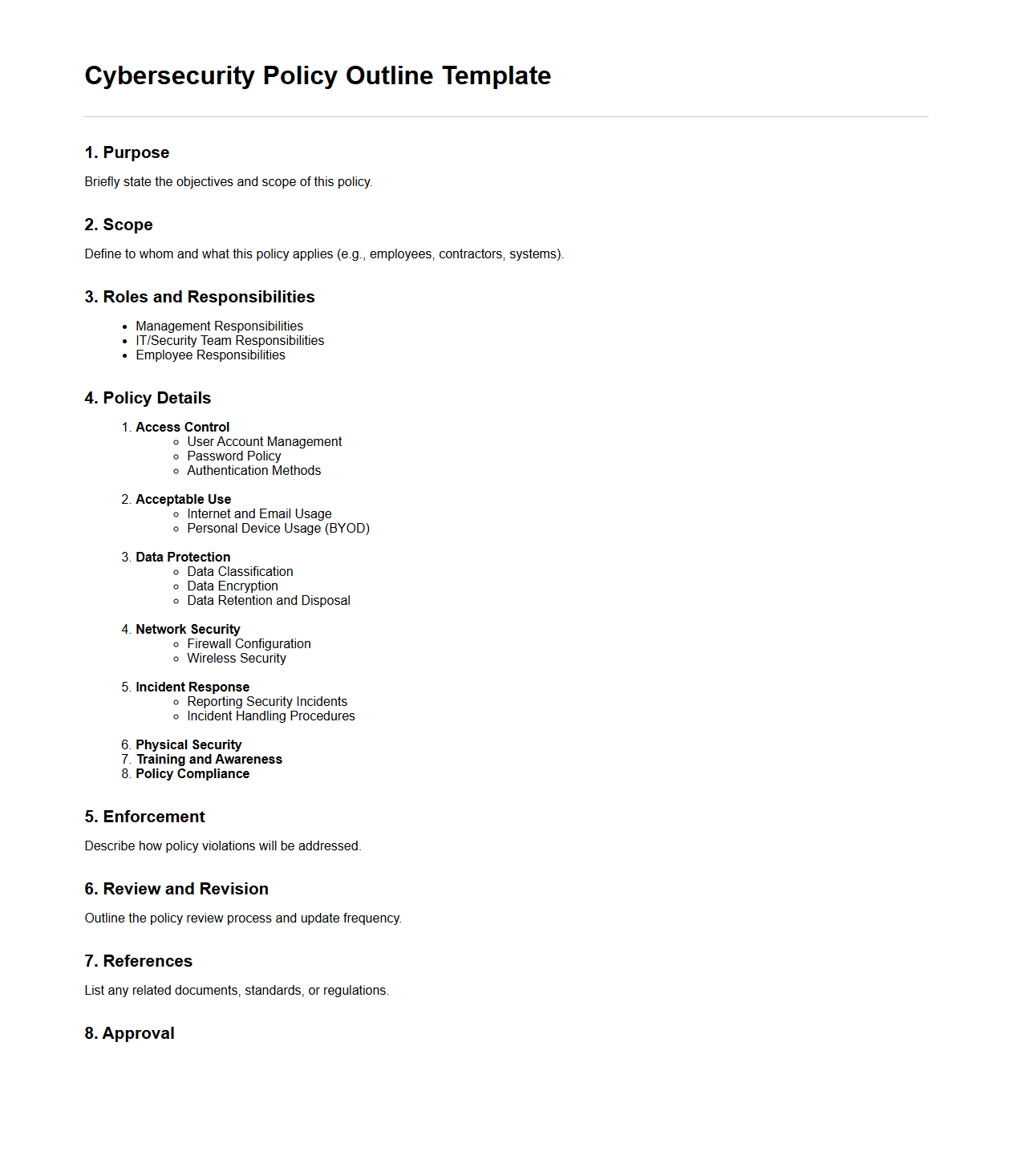
Cybersecurity Policy Outline Template
A
Cybersecurity Policy Outline Template document serves as a structured framework that organizations use to develop comprehensive cybersecurity policies. It typically includes essential components such as roles and responsibilities, access controls, incident response procedures, and compliance requirements. This template streamlines the creation of consistent and effective security guidelines to protect sensitive data and mitigate cyber risks.
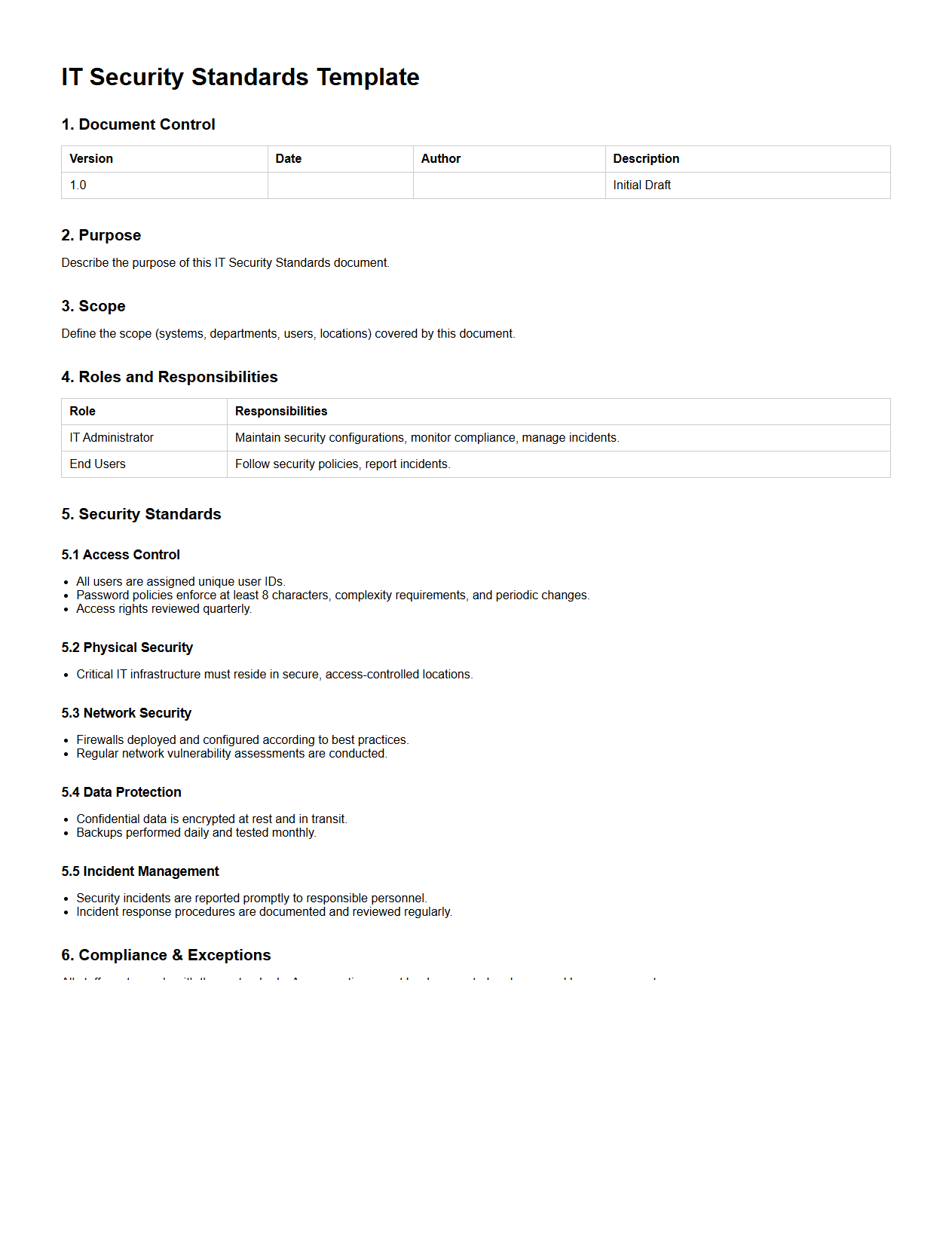
IT Security Standards Template
An
IT Security Standards Template document serves as a structured framework outlining the essential policies, protocols, and best practices required to protect an organization's information systems from cyber threats. It provides detailed guidelines on access control, data encryption, incident response, and compliance requirements to ensure consistent and effective security measures across all IT operations. This template helps organizations maintain regulatory compliance, reduce vulnerabilities, and establish a baseline for evaluating and improving their cybersecurity posture.
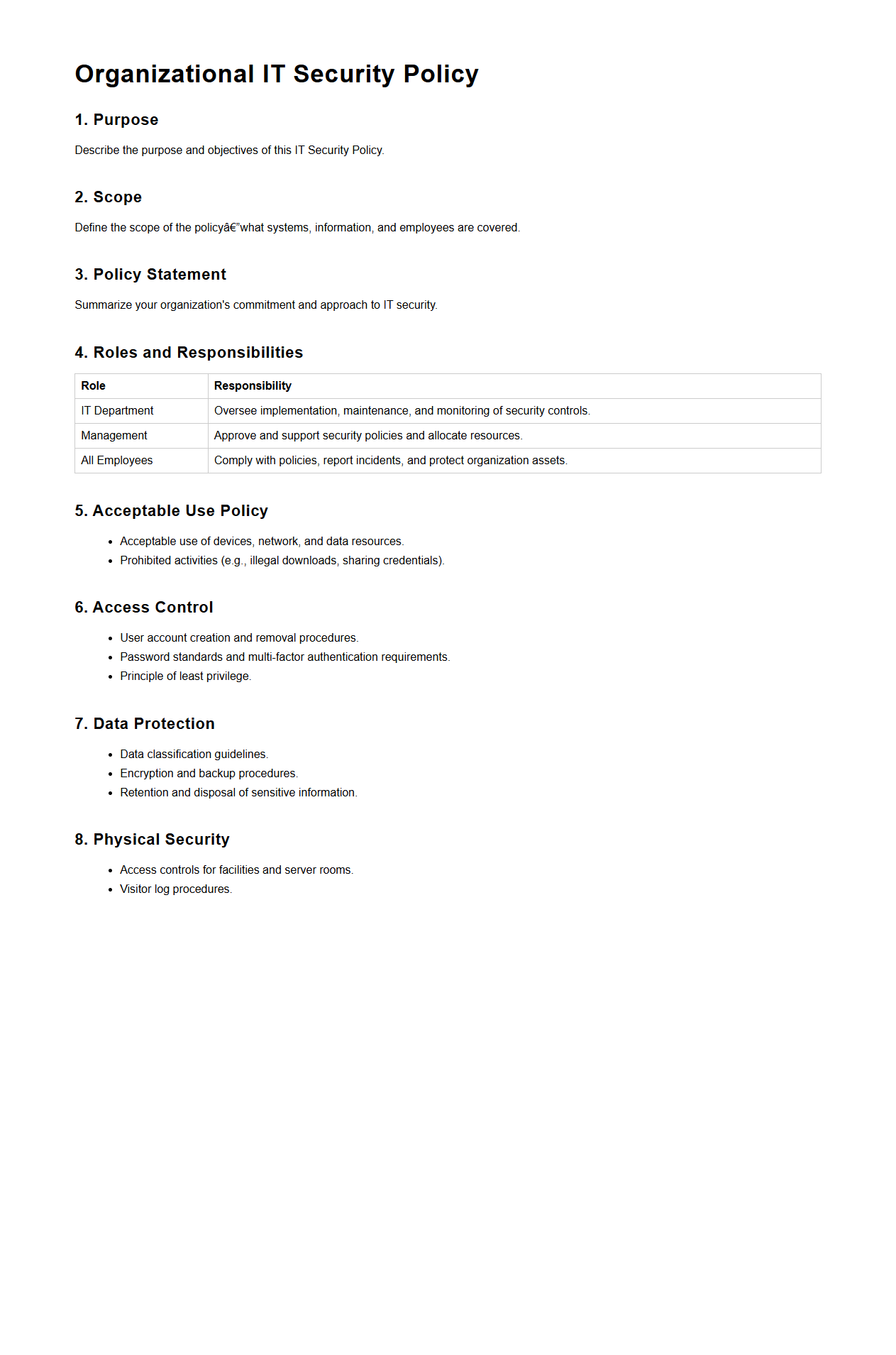
Organizational IT Security Policy Format
An
Organizational IT Security Policy Format document outlines the structured framework used to define and implement security measures within an organization. It typically includes sections such as purpose, scope, roles and responsibilities, acceptable use guidelines, data protection protocols, and incident response procedures to ensure comprehensive IT security management. This format ensures consistency, compliance with regulations, and clarity in communicating security expectations across all employees and stakeholders.
Company IT Security Policy Draft
A
Company IT Security Policy Draft document outlines preliminary rules and guidelines designed to protect an organization's information technology assets, including hardware, software, and data from unauthorized access or breaches. It serves as a foundational framework for cybersecurity measures, detailing employee responsibilities, access controls, and incident response protocols. This draft is essential for aligning IT security practices with industry standards and regulatory compliance requirements.
IT Data Protection Policy Template
An
IT Data Protection Policy Template document serves as a structured framework to outline an organization's guidelines and procedures for safeguarding sensitive data. It establishes protocols for data handling, access control, encryption, and breach response, ensuring compliance with relevant data protection regulations such as GDPR or HIPAA. This template aids in standardizing data security practices, minimizing risks of data loss, unauthorized access, and ensuring accountability across IT operations.
Network Security Policy Template
A
Network Security Policy Template document provides a structured framework for defining an organization's rules and procedures to protect its network infrastructure from unauthorized access, cyber threats, and data breaches. It typically outlines access controls, user responsibilities, incident response protocols, and compliance requirements to ensure consistent enforcement of security measures. By standardizing security practices, it helps organizations maintain robust defenses and regulatory adherence across all network environments.
IT Security Compliance Policy Example
An
IT Security Compliance Policy Example document outlines the specific rules and guidelines organizations must follow to protect information systems and ensure adherence to regulatory standards. It details security controls, risk management procedures, and employee responsibilities to maintain data confidentiality, integrity, and availability. This policy serves as a reference for implementing effective cybersecurity measures and achieving compliance with industry regulations such as GDPR, HIPAA, or PCI DSS.
Information Technology Security Procedures Template
An
Information Technology Security Procedures Template document provides a structured framework for defining and implementing security measures within an organization's IT environment. It outlines step-by-step guidelines to protect data, networks, and systems from unauthorized access, cyber threats, and vulnerabilities. This template ensures consistency in applying security protocols and helps maintain compliance with regulatory standards.
What key elements should a blank policy template for IT security documentation include?
A blank policy template for IT security documentation should include clear sections on purpose, scope, and responsibilities to provide comprehensive guidance. It must define security controls, access management protocols, and data protection measures to ensure robust security standards. Additionally, including compliance requirements and procedures for incident reporting fortifies the policy's effectiveness across the organization.
How does a blank IT security policy address employee access control procedures?
The blank IT security policy incorporates detailed access control procedures by specifying user authentication, authorization levels, and role-based access controls. It outlines steps for granting, modifying, and revoking employee access to sensitive systems and data. This ensures that only authorized personnel can access critical information, minimizing the risk of unauthorized breaches.
What regulatory compliance considerations must be reflected in an IT security policy draft?
An IT security policy draft must include adherence to relevant regulatory compliance frameworks such as GDPR, HIPAA, or PCI-DSS, depending on the industry and jurisdiction. It should define data privacy requirements, audit trails, and reporting obligations to ensure legal conformity. Addressing compliance helps organizations avoid penalties and maintain trust with stakeholders.
How should incident response guidelines be structured in a blank security policy document?
Incident response guidelines in a blank security policy must be clearly structured with defined phases: preparation, detection, containment, eradication, and recovery. Roles and responsibilities of the incident response team should be explicitly assigned to streamline handling and communication. Comprehensive documentation and post-incident review processes must also be part of the guidelines to improve future responses.
What are essential review and update frequencies outlined in a baseline IT security policy?
A baseline IT security policy should mandate regular review and updates, typically on an annual basis or after significant security incidents. It should also require reviews whenever there are changes to technology, regulatory requirements, or organizational structure. Consistent updates ensure the policy remains relevant and effective against evolving cybersecurity threats.